IDS Vs. IPS – What You Need to Know
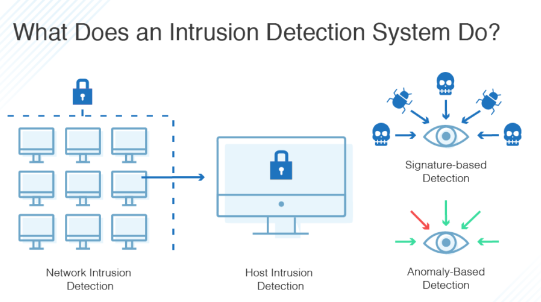
IDS and IPS are network security tools that monitor traffic for suspicious or anomalous activity. They identify potential threats by comparing incoming network packets to information from a database of known threats or suspicious patterns.
IDS systems generate alerts upon detection but don’t take any proactive action themselves. A security analyst must analyze these alerts and decide what to do next.
The tools most frequently used for this purpose are intrusion detection systems (IDS) and intrusion prevention systems (IPS). It’s crucial to understand how IDS vs IPS differ, which ones work best for particular kinds of companies, and how to make the most of each one’s potential.
IDS is passive
An Intrusion Detection System (IDS) watches network traffic in motion to log suspected threats and raise alerts. IDSs can also modify firewall access control lists or close processes on a compromised system to thwart or block attacks.
IDSs that rely on machine learning can compare new behavior to verified trust models and identify unknown attack types. These systems can detect anomalous traffic from new devices or users trying to access sensitive systems.
IPS monitors traffic inside a network, using hundreds of rules to decide whether to drop or let a packet pass through. They look for specific bytes or instruction sequences that indicate malware or other malicious activity. They can be less effective against hackers that use signature-based attacks.
Another type of IDS, called an Anomaly-based IDS, uses machine learning to establish a model of normal behavior for the system. It can then compare new behavior to that model to determine whether it is suspicious or healthy.
The system is prone to false positives and may report an attack when it doesn’t exist. Some companies use a hybrid IDS to avoid false positives and other issues that can arise with a single solution.
Choosing an IDS that suits your organization’s needs is essential. Then, it’s necessary to test the solution regularly and evolve your testing approach to keep up with changes in security threats.
IPS is active
IPS is a system that scans traffic and takes action automatically when it detects a threat. Unlike an intrusion detection system, which sits behind a firewall, an IPS is in line between the source and destination networks.
Depending on the vendor, there are different types of IPS. Network-based IPS can look at network traffic and file integrity, while host-based tools can monitor a host or server’s entire infrastructure.
Both IPS technologies use signatures that describe attacks and can be matched to network packets and logs. The signatures are compiled from a long list of known threats and vulnerabilities.
While signature-based detection helps identify new attacks, it can cause false positives when legitimate packets are mislabeled as malicious. Another IPS technique, statistical anomaly detection, randomly samples network traffic and compares it to performance-level baselines. If a packet is deemed outside the baseline, it triggers an IPS rule that causes traffic to be dropped or blocked.
When an IPS is configured to block traffic, it may slow down network performance. This is particularly common when multiple IPSes are deployed in a network.
IPSes can also block legitimate traffic, which leads to a Denial of Service (DoS) to legitimate users. The best way to avoid this is to keep IPSes after the firewall so only traffic from trusted hosts can pass through.
IDS is prone to false positives
False positives are a significant concern for security professionals and can significantly impact an organization’s ability to protect data. These false alerts can be challenging to weed out, as various factors typically generate them.
The key is to have a process that limits the number of false positives while giving users the information they need to take action. In addition to implementing a policy for suppressing IDS alerts that aren’t malicious, security staff may also reduce the number of false positives in their detection rules by tweaking them. This may include adjusting the frequency of vulnerability scanner updates and adding exception management to IDS alerts.
Whether your IDS is running on-premises or cloud-based, security information event management (SIEM) / log management systems can alleviate the problem by automatically tagging specific IDS false favorable conditions via event correlation and exception management. SIEMs can easily tag IDS incidents in real-time based on current configurations, patches and other non-threat events such as scheduled vulnerability scans.
IPS is prone to false negatives
IPS technology watches packet flows and can detect and stop attacks such as brute force and Denial of Service (DoS) attacks. It can also identify and block vulnerability exploits, which are attacks that use an existent software vulnerability to gain control of an endpoint device.
These techniques can be used to identify threats but can also be prone to false positives. This can impact your organization because the IPS might decide to shut down a network or drop traffic between specific devices, even if it didn’t need to.
Because of this, it’s essential to select an IPS solution backed by solid security policies. These policies can prevent a single false negative from causing the most damage.
IPS systems use either signature-based or anomaly-based detection to detect threats. Signature-based detection looks for packets with malicious or exploit-specific signatures, while anomaly-based detection compares network traffic against a pre-defined baseline. In addition, many IPS systems employ deep inline learning to enhance detection and accurately identify never-before-seen malicious traffic without relying on signatures.